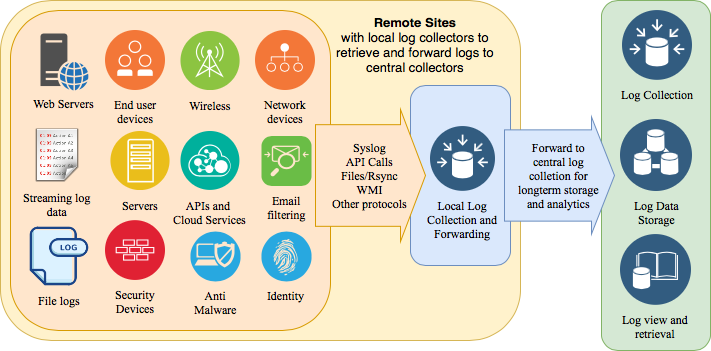
Collecting and processing security logs is one of the primary function of any SOC. Log sources vary widely, starting from security device logs, network components, applications, servers and many others. Collecting logs also needs significant investment in log storage and processing infrastructure. You want to prioritize log sources that bring the most value from security monitoring perspective. For these reasons, you should start with a small subset of log sources and expand the scope of log collection over time (in future phases of the project). While defining the scope of log collection for each phase, you can consider the following:
- Value of particular log source for identifying security events and detecting noticeable incidents (proactive).
- How a particular log source can help in incident investigations (reactive).
- Amount of log data that you can handle, both from analytics and storage perspectives.
- Compliance needs and requirements that a particular log source fulfills.
Typically, you should start with logs coming from security devices (firewalls, IDS, content filtering and proxy servers, identity management systems, proxies, VPN concentrators, end-point detection and response systems, etc.). The second preference may be server operating systems and public facing web server logs. Then you can move to applications, and so on. There is no prescribed order and you should define your own scope based upon your particular situation and which systems play a key role inside your organization.
With most of the organizations moving to Cloud, collecting logs from Cloud service providers like AWS, Azure, Google and others could become a priority for some organizations. Additionally, if you are using a Cloud Access Security Broker (CASB), collecting logs from CASB system in the initial phases of SOC implementation will also be a good idea.
For some manufacturing organizations, logs from IoT devices and operational technologies could provide significant value. Auto manufacturers could be interested in logs from connected vehicles.
You can also use threat modeling techniques to identify critical log sources and prioritize these accordingly.