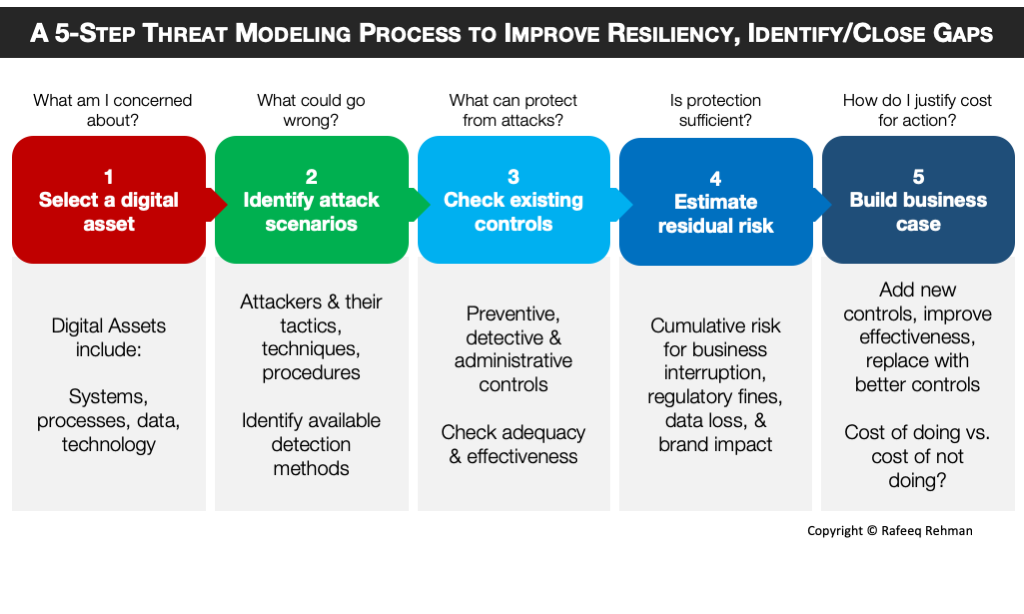
Many organizations with mature Cybersecurity program have implemented controls to safeguard their digital assets. However, controls can give a false sense of security as many times mere existence of a control does not mean that it is (a) adequate and/or (b) effective. Protecting crown jewels requires continuous monitoring and evaluating controls. Following is a 5-step threat modeling process to improve resiliency of your program, identify gaps and close these gaps. The process starts from identifying the digital assets you are most concerned about and potential attack scenarios and ends at building a business case to close any identified gaps.
Step 1 – What am I concerned about?
A typical starting point for threat modeling is to identify digital assets that you are more concerned about. A digital asset may be in different forms. It could be an overall system crucial for your business, a process, a data store where business critical data is stored, a specific piece of technology and so on. The important thing is that you select an asset based upon criticality to business operations. Some people may refer to the critical business assets as “crown jewels”.
Step 2 – What could go wrong?
Once you have a digital asset identified, the next step is to brainstorm about:
- Who are potential threat actors (internal, external, partners, state sponsored, hectivists, financially motivated, corporate espionage, etc.)?
- Attack methods used by these threat actors (hacking, phishing, malware, physical, and others?
- How these attacks will manifest in detection mechanisms (logs, behavior/anamolies, network traffic etc.)?
Step 3 – What can protect from attack?
Here you are going to evaluate all controls in place to prevent and/or detect the attacks. These controls could be different flavors:
- Preventive controls that stop something bad from happening (firewalls, end point protection, IPS, etc.)
- Detective Controls like IDS, SIEM and others
- Administrative controls like policies, awareness programs
The important thing is to make sure that controls are (a) adequate and (b) effective. A firewall may be present but may not be properly configured. Similarly you may be using encryption but not managing keys properly. These are the examples where controls exist but not effective.
Step 4 – Is protection sufficient?
Based upon adequacy and evaluation of existing controls, you can estimate residual risk of a breach that may include a sum of multiple risk factors, including but not limited to:
- Business interruption risk
- Regulatory fines from different government agencies (e.g. Federal Trade Commission and SEC) or industry groups like PCI.
- Risk of data loss
- Impact to brand value
Step 5: How do I justify cost?
Creating a business case is one of the best ways to justify investment in Cybersecurity. Why you need funding? It may be for one of the following purposes:
- Add a new control because none exists
- Improve effectiveness of an existing control
- Replace an existing control with a better one
While there are many templates and recommendations about building business cases, one simple way is to focus on cost of doing it vs. cost of not doing it. There is a cost in both ways and if your cost of doing it is lower, only then it makes sense to request for funding. One template that I like is 9-stage business model by Chris Luxford.
How to use this approach?
I use this process in the form of a workshop, three to four hours long. My recommendation is that the exercise should be carried out throughout the year, may be once a month or at least every quarter, selecting a different digital asset each time or picking a different scenario for the same digital asset.