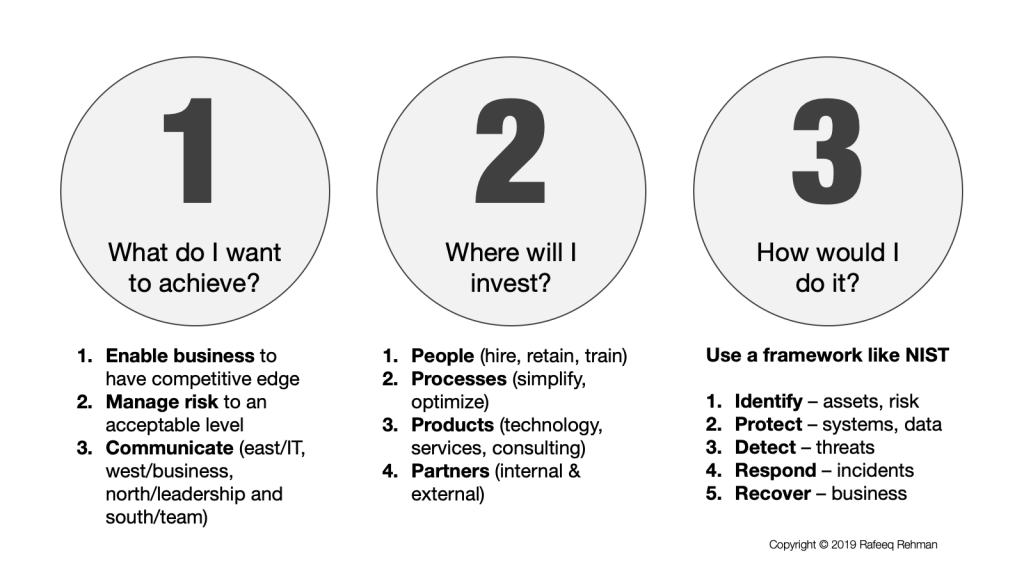
Many CISOs and Infosec leaders I meet face continuous challenge to communicate their strategy that is simple and others can understand and relate to. I have created a simple model for CISOs to explain it on a single page and have found it to be an effective tool. Part of this is based on NIST Cybersecurity framework.
The strategy has three parts:
- What do I want to achieve?
- Where will I invest – both time and money?
- How would I do it?
What do I want to achieve?
Communicating your objectives in clear, concise and easy-to-understand manner that others can relate to is key to success of a CISO. Here are three key objectives:
- Enable business to gain competitive edge and using security as an enabler.
- Manage risk to an acceptable level
- Communicate continuously with and East/West/North/South model. The East represents other IT teams. The West includes business leaders within your organization. The North refers to executive leadership and board. The South means that you communicate continuously with your own team.
Where will I invest?
This is both about time and money investments and falls into the following four areas:
- People – People being the most important part of any security program and investing in hiring the best, retain the talent, and train security teams on the latest technologies.
- Processes – This is about simplifying and optimizing processes to achieve some goals without relying to fix everything using technology. According to a quote from Bruce Schneier, “If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology”.
- Products – Here you would look at technology, services, consulting from different vendors.
- Partners – Spending time and energy in building partnerships with both internal teams and external vendors.
How would I do it?
It is a great idea to pick a framework to communicate how would you achieve your objectives. I like NIST Cybersecurity Framework but you can choose a different one based upon you needs. I prefer NIST because many organizations follow it and it fits well into explaining your strategy. With this framework, you have talk about business outcomes in the following five areas:
- Identify – assets and risk that face your organization, build a governance model
- Protect – systems, data, and other digital assets
- Detect – threats using a number of methods including but not limited to logs, anomalies, network, threat intelligence and others.
- Respond – to incidents quickly and effectively
- Recover – business quickly after a security incident
Why name it 3-3-4-5 model?
I named it 3-3-4-5 model because it has three parts. The first part includes 3 components, the second one 4 components and the third one 5 components.