I am not telling you anything new when I say that an essential part of a CISO’s job is to build a Cybersecurity program, communicate it to stakeholders, and continuously tweak it based upon continuously changing threat landscape. Job of a CISO is complex as shown in CISO MindMap for many years and it is getting even more complicated. This article is describe some tools that will help overcome some complexities, build a roadmap and request funding using a simple business case model.
Whether you are building a brand new Cybersecurity program or want to make some changes to improve an existing one, I have found the following tools very useful. These will help you in identifying areas you need to work on, communicate to stakeholders and request funding by building compelling business cases.
MITRE ATT&CK
Mitre ATT&CK is knowledge base of adversary tactics, techniques, and procedures (TTP). While there are many ways to use ATT&CK, using it for an assessment of your Cyber defense capability is one of the important ones. In the framework, there are twelve main areas of tactics and a number of techniques under each of these areas. ATT&CK Navigator is a great tool to start assessment of your current capability of defending against different types of attacks, find gaps, and adjust your strategy and roadmap accordingly.
Following is a screenshot of ATT&CK Navigator where you can use it for assessment, color code your capabilities, identify gaps, and use it as a communication tool.

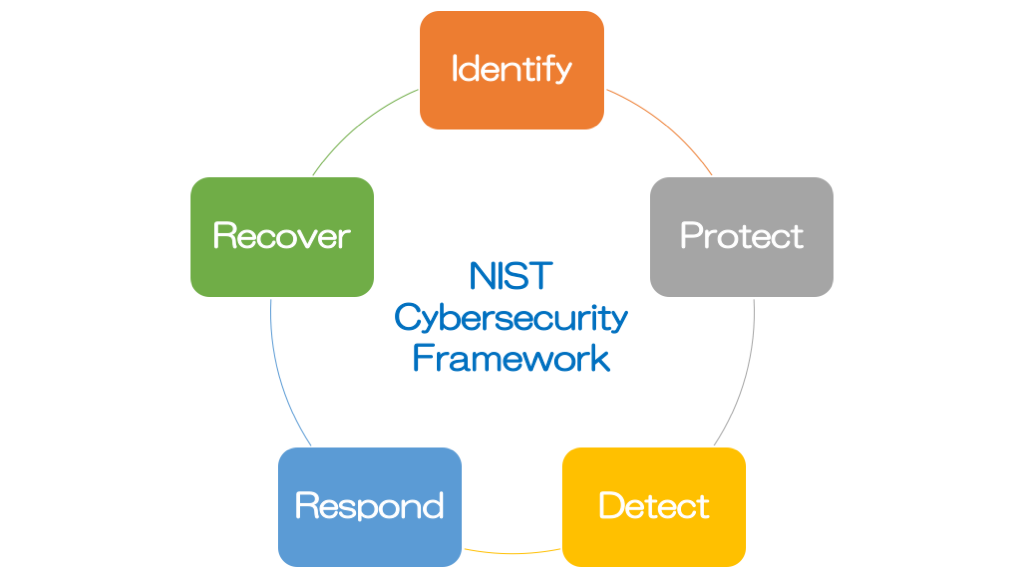
Use of NIST Cybersecurity Framework
NIST Cybersecurity Framework is an outcome of collaboration among government, universities/academia and industry. It provides five functions and helps you balance your efforts to cover all aspects of building an effective cybersecurity program. These functions help you organize your activities and create a balanced approach towards different aspects of a meaningful program. The functions are listed below:
- Identify – Understand what you have and includes activities such as asset management, governance, risk assessment.
- Protect – Build safeguards and controls to protect what is important to you.
- Detect – Implement capabilities to identify security events and incidents.
- Respond – When an incident happens, be ready to respond, have appropriate processes, training and tools.
- Recover – Ensure resilience of your systems in the face of incidents and build capability to quickly recover from the impact of these incidents.
There are many success stories about how different organizations have used NIST framework and I am sure some of these will be interesting for you.
CISO MindMap as Communication Tool
Over a number of years, I developed CISO MindMap to describe complexities of job that security professionals and leaders have to deal with on a daily basis. Since then, this MindMap has been adopted by many leaders and organizations. SANS adopted it for training program and published Leadership poster based upon it.
CISO MindMap is a great tool for communicating security programs and complexities of your job to different stakeholders.
Request Funding with 9 Stage Business Case Model
Justifying investment in Cybersecurity and developing a business case is not always straight-forward arithmetic. I have found 9-stage business model by Chris Luxford as one of the great tools. Use it as a single-page business case template and attach it with your funding request. Focus on cost of doing something vs. cost of not doing it.
Balancing Budget
Depending upon where you are in your journey of implementing your security program, your budget may be skewed in certain direction. However, a good advice is to balance it between the following three areas (three Ps):
- People – salary and benefits, training & development
- Products – purchase tools and technologies
- Partners – contract third parties for services that you don’t want to build in-house and that are rarely used
While there are many ways to build and execute a security program and roadmap, I am confident that the above tools are only going to help you continuously improve your Cybersecurity practice and make you successful as a leader.
Subscribe to this blog
References
- CISO MindMap 2020 – https://rafeeqrehman.com/2020/06/12/ciso-mindmap-2020-what-do-infosec-professionals-really-do/
- CISO MindMap 2019 – What do InfoSec professionals really do? http://rafeeqrehman.com/2019/08/25/ciso-mindmap-2019/
- Mitre ATT&CK – https://attack.mitre.org/
- ATT&CK Navigator – https://mitre-attack.github.io/attack-navigator/enterprise/
- Model Monday – 9 Stage Business Case – https://www.linkedin.com/pulse/model-monday-9-stage-business-case-chris-luxford/
- NIST Cybersecurity Framework – https://www.nist.gov/cyberframework
- NIST Framework success stories – https://www.nist.gov/cyberframework/success-stories
- SANS Leadership Poster based upon CISO MindMap – https://www.sans.org/security-resources/posters/security-leadership-poster/135/download