Whether it is opening a firewall port, relaxing a permission on an S3 bucket, or mailing a confidential document to a private email address, people often try to circumvent information security controls with a “good intention of getting things done”. Unfortunately, the same results in data breaches repeatedly, many of which could be avoidable. One of the reasons is how the CIA (Confidentiality, Integrity, Availability) triad is used by information security professionals to design security controls. An overemphasis on the CIA triad makes information security professionals forget the harm some of these controls may do to human experience and create an implicit temptation for others to circumvent those controls. It is time to recognize this issue and make modifications to remediate it.
What is the CIA triad of information security?
The triad is built around fundamental principles and objectives of any information security program. It has done an excellent job to explain information security to newcomers to the field and explain security objectives to others.
In summary:
- Confidentiality is about ensuring that information stays protected and is only disclosed to people who need to know it.
- Integrity is built around the idea that no unauthorized change is made to the information, systems and networks to protect confidence in the accuracy of the information and other IT systems.
- Availability – The information, systems, networks and other resources stay available in the face of cyber attacks, natural disasters, and other unforeseen events.
There are numerous articles written on this topic and I am not going to go into detail except stating one crucial aspect: A balance is needed in all three parts of the triad as overemphasis on one can impact the others. For example, over-protection of confidentiality may adversely impact availability.
Without good human experience, the triad is failing the profession
One way or the other, directly or indirectly, ultimately people have to interact with security controls designed by the information security departments. As we are painfully aware of the fact that many times security teams are considered a roadblock rather than enabler of the business because of these controls. I am sure many of us have heard quotes like “security is where ideas go to die”. If you dig deeper into this notion and ask questions to explore why it is so, you will easily come to realize that the missing element in designing security controls is forgetting the human experience.
With very good intentions and without any disregard to human experience, sometimes security professionals still get carried away with strict implementation of the CIA triad in the design of security controls. The reason is that the human aspect is not part of basic principles and objectives (Confidentiality, Integrity and Availability). Since the CIA triad is always the focus of designing these controls, it is time to change it.
How can we redefine the information security triad?
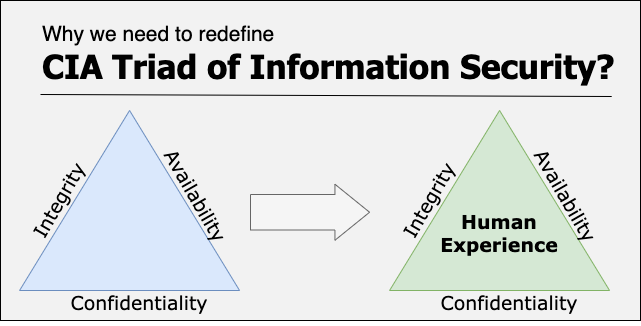
While there could be a number of different ways to bring the notion of human experience into the CIA triad, one of the simpler ones can be putting the human experience at the center as shown in the diagram below.
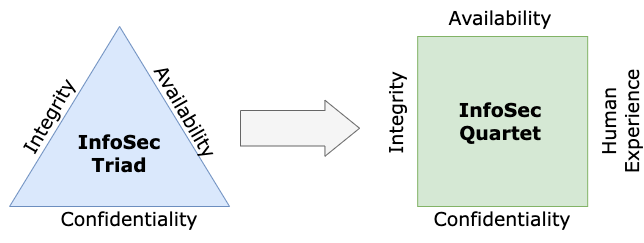
Another option is to change the triad to a quartet. The importance of factoring in the human experience is high enough to make this change.
Now just changing the triad one way or the other is not enough unless it is accompanied by making it part of security training and defining what the human experience means and how it is impacted, positively or negatively, by certain actions. Major security certification organizations like ISC2, ISACA and others also need to make it part of the learning objectives for certifications exams.
Continuous improvement to the information security profession based upon what we learn from our experiences is an essential part of the progress. Lack of considerations for the human experience is a deficiency in the current state of affairs and it needs to be addressed, starting with fundamental change to the information security triad.