NOTE: An updated version of CISO MindMap has been published here.
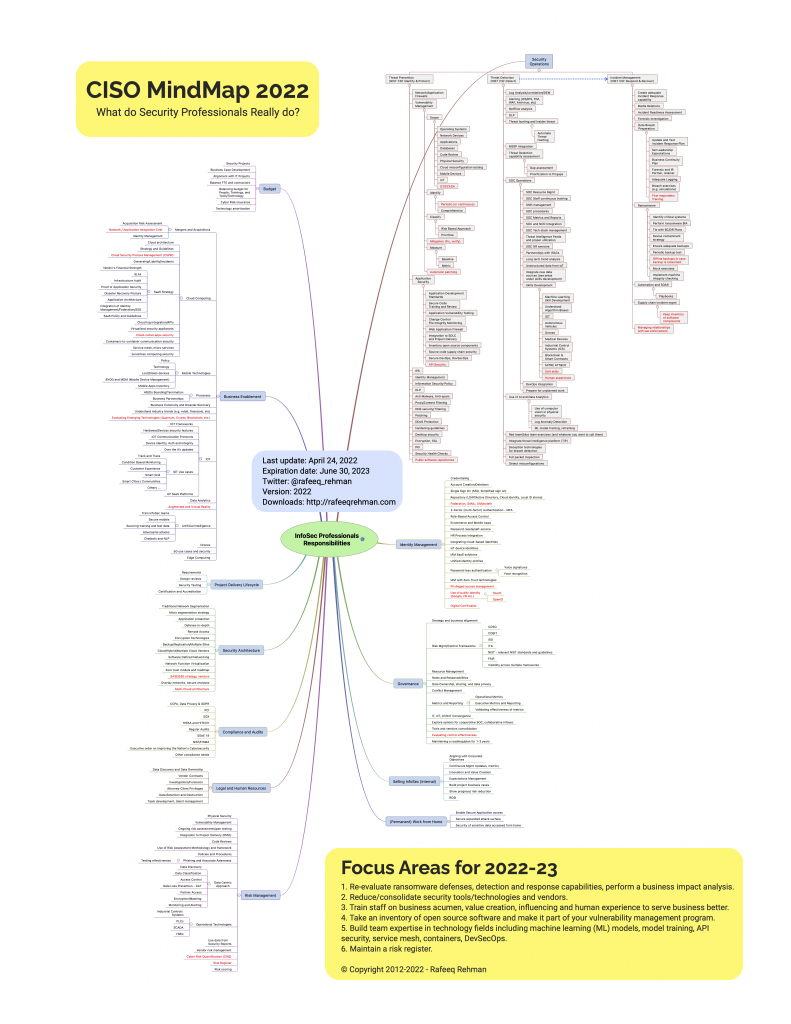
Let me start with the quote from last year: Most people outside the Cybersecurity profession don’t fully realize and appreciate the complexity of a security professional’s job. Since 2012, CISO MindMap has been an effective educational tool and has enabled professionals to design and refine their security programs. Here is the latest and updated CISO MindMap for 2022 with a number of updates and new recommendations for 2022-23.
Please download PDF version for better printing quality.
What has changed?
With time, the responsibilities of security professionals are only increasing. Why? Technology is changing fast, bringing new ways of doing business, continuous adoption of Cloud, and many emerging technologies. Not only the Infosec professionals are “expected” to deeply understand these technologies, but also provide policies/guidance on how to secure them. For this reason, every year you find a few new things on the CISO MindMap. Like every year, few things are added, changed or removed from the MindMap depending upon their relevance. Changed items are marked in red for your convenience.
Other changes include but not limited to:
- Remove duplicates
- Merge branches with overlapping functions
- Add NIST CSF references at high level, where possible.
- In some cases more defined/accepted terminology has emerged. For example, Cloud Security Posture Management (CSPM) is a widely accepted term now. As a result, I have replaced some Cloud Security items with CSPM.
- Expiration Date – A common issue is that many professionals still have older CISO MindMap copies. I added an “expiration date” to let people know when they should stop using a particular version. The expiration date for the 2022 version is the end of June 2023. The next version will be published before the current version expires.
Recommendations for 2022-2023
I know you already get plenty of recommendations from your vendors, industry analysts and pundits, and other “experts”. You also know that many of these recommendations may have some vested interests and/or biases. I make my own recommendations as a practitioner every year and try to be objective, avoid the hype, need for adoption in the next 12-18 months, and solely focus on what data and research shows. However, it is still my interpretation of data and facts and I may have my own unintended biases even with all objectivity and an evidence-based approach. For me, the most difficult part while making these recommendations is to pick as few as I can. The following list is longer than what I would like it to be but hopefully it would give you a few things to think about. The followers of MindMap would quickly realize that some of these are the same as of last year.
- Re-evaluate ransomware defenses, detection and response capabilities, perform a business impact analysis and identify critical processes, applications and data.
- Reduce/consolidate security tools/technologies and vendors. More tools don’t necessarily reduce risk but do add the need for maintaining expertise on security teams.
- Train staff on business acumen, value creation, influencing and human experience to serve business better. I can’t emphasize this enough.
- Take an inventory of open source software (both direct and indirect use) and make it part of your vulnerability management program.
- Build team expertise in technology fields including machine learning (ML) models, model training, API security, service mesh, containers, DevSecOps.
- Maintain a risk register.
I am eager to listen to your viewpoint on these recommendations, why or why not!
How to use CISO MindMap?
I receive messages from many professionals about how many different ways they are using the CISO MindMap. Over the years, it has become a great tool for many of you and I appreciate your feedback and kudos. Following are some of the ways this MindMap is quite helpful:
- Have you been asked what you really do as a security professional? The CISO MindMap is one way for answering the question and explaining it to people. I have heard from many professionals that this MindMap is extremely helpful in explaining the complexity of a CISO job, especially to a business audience.
- A means for guiding conversation with other technology professionals.
- SANS Institute uses it as part of the Security Leadership Poster.
- Designing and refining security programs.
- Some security vendors use the MindMap for awareness.
- CISO group discussions and/or community meetings.
Obviously there is a lot on this MindMap. The stress on people who have these responsibilities is real. If nothing else, this MindMap should help leaders recognize that stress and do something about it. I covered this topic (stress) in my latest book Cybersecurity Arm Wrestling: Winning the perpetual fight against crime by building a modern Security Operations Center (SOC) as well.
Translation to other languages
Some of you have offered to translate the MindMap into other languages. I really appreciate it and look forward to working with you to have a few translations completed this year.
Acknowledgments
Many people have contributed to the thought process behind this MindMap over the years. This time we had a LinkedIn Group to gather suggestions and comments from the community. While many provided feedback, the following is an alphabetically organized list of people and organizations who provided “specific suggestions” for improvements. If I missed anyone, please send me a message to make corrections.
- Ahmed Kamel
- Alan Ng
- Aldo Febro
- Alexandra Gobbi
- Atif Yusuf
- Christophe Reverd
- CISOS CLUB
- Gareth Williams
- George Johnson
- Indy Dhami
- Johann Balaguer
- Matthew Thompson
- Phillip Crump
- Rodolphe Simonetti
- Ryan Guzal
- Shaun Van Niekerk
- Shrinivas Kulkarni
- Steve Cook
- Walter Heffel
Your suggestions contributed towards overall enrichment of the MindMap. Additionally, I am thankful to all community members who use and share their experiences. Your input is highly appreciated!
Copyright © Note
This MindMap is copyrighted material. However it is absolutely free to all (like water and air) with no strings attached, as long as it is not altered and not used to make money. When using this MindMap, please cite the source properly so that recipients can receive future updates.