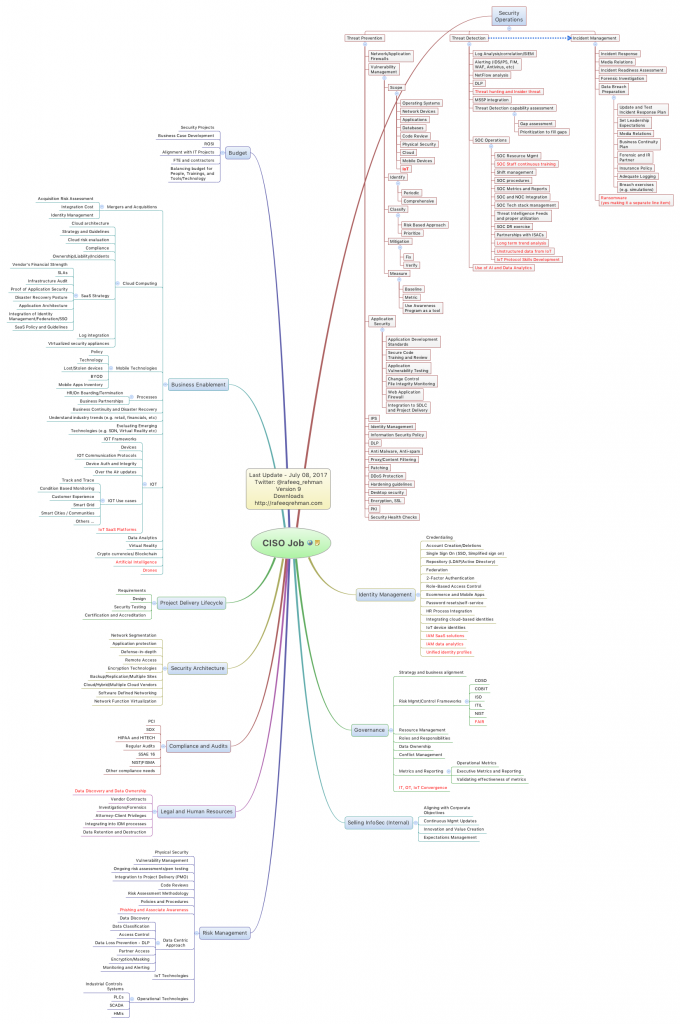
Note: An updated version of CISO MindMap (2018) is published here
While Ransomware may be the talk of the town these days, many other profound changes are happening in the industry that impact job of information security professionals. Keeping in view these change, I felt a need for updating CISO MindMap. The new and updated CISO MindMap 2017 is attached below. This time, I have highlighted all changes in red color to make it easy for those who have been following this CISO MindMap for some time.
One major change is about IoT, keeping in view that more and more companies see value and are adopting IoT technologies. Lines between IoT, Industrial IoT, and industrial control systems are blurring gradually. Security professionals are being called in to respond to IoT incidents, which are increasing over time. The IoT vendors are in infancy from security perspective in many cases, with lax security controls. I feel there is a need for all organizations to include IoT as an essential part of their overall security operations. With a little research inside their organization, they may be surprised how many IoT technologies are already being used by their businesses that they may not be aware of.
I also believe that InfoSec professionals should make subjects such as artificial intelligence, drones, sharing economy, and data analytics as part of their learning goals. InfoSec is an essential enabler for modern businesses and we, as a community, should be at the forefront of this progress instead of standing in the way.
Last but not the least, InfoSec professionals must keep a better “Customer Experience” as a guiding principle of everything they do. I would recommend taking a short course on “design thinking” methodology that would make people think and act differently and more productively. We must improve our brand!
Like always, feel free to provide your feedback and comments. Also, register on this blog to keep updated. You can also download PDF version of the CISO MindMap.
Your feedback is welcomed on my Twitter handle at @rafeeq_rehman
References
- Building a Successful Security Operations Center: Part 1
- Building a Successful Security Operations Center: Part 2, Estimating SOC Budget
- Building a Successful Security Operations Center Part 3: SOC Budget Calculator
- Building a Successful Security Operations Center Part 4: Defining SOC Scope