Note: An updated version of this article is available now. Please click here to go to CISO MindMap 2020 version.
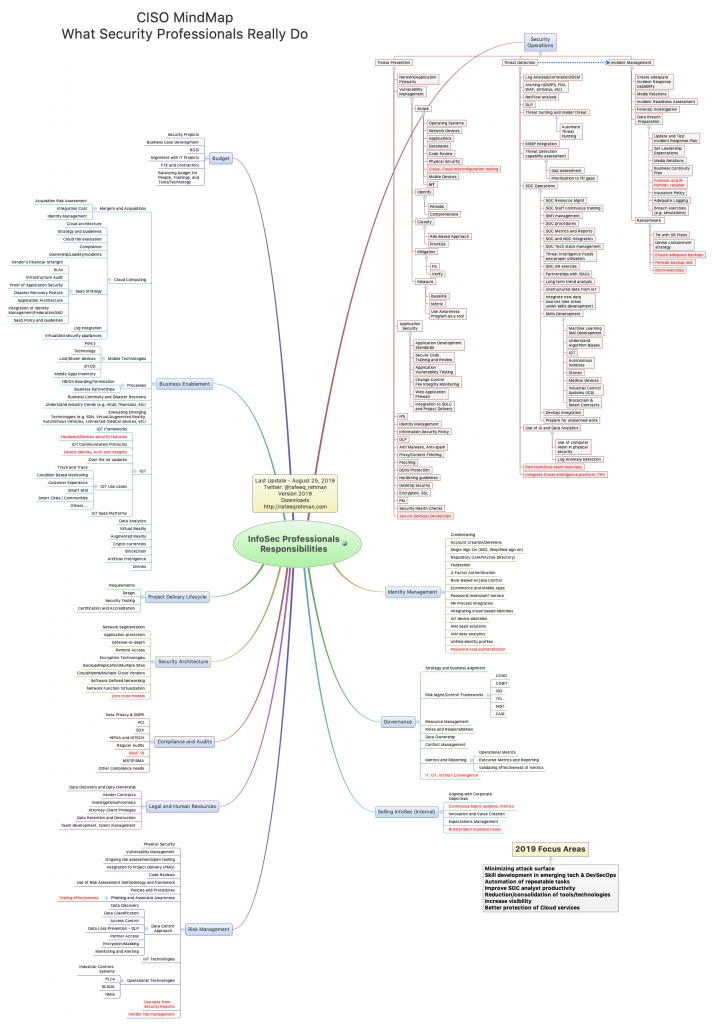
Just like other areas of information technology, information security landscape continues to change at a fast pace. The updated CISO MindMap for 2019 covers important changes in the security landscape. In some bright areas, technologies using machine learning (ML) to detect zero day attacks are getting better and integrating of threat intelligence platforms with security operations is making analysts’ job easier. However, a lot more work is needed to avoid errors in misconfiguration of Cloud services.
Download PDF version of CISO MindMap 2019
How to Use CISO MindMap?
How many times people ask you about what you really do? Although the answer could be many things depending upon the context of the question and who is asking it, sending a copy of this MindMap could help. I have heard from many professionals that this MindMap is also helpful in explaining the complexity of a CISO job.
What is New?
There are some items in the MindMap marked in red color. These are either new or modified compared to 2018 MindMap. Also, take a look at the bottom-right box marked as “2019 Focus Areas” which lists some of the areas of your responsibility that you should pay attention to.
Following are some areas where I would recommend more focus for the remainder of the year 2019 and for planning next year activities:
- Minimizing attack surface
- Skill development in emerging tech & DevSecOps
- Automation of repeatable tasks
- Improve SOC analyst productivity
- Reduction/consolidation of tools/technologies
- Increase visibility
- Better protection of Cloud services
Comments and Suggestions – Feel free to send your feedback on my Twitter handle @rafeeq_rehman
Using as Poster, Derived Work, or Commercial Use – This is a copyright material but is made free for non-commercial use as long as the source is properly cited and the MindMap is not altered. Please contact me if you want to use this as a poster for your education and awareness programs or for any educational purposes. Any derived work or commercial use requires written permission of the author.