Once SOC analysts declare an event as a security incident, the CSIRT takes the ownership of the incident, take necessary actions and close it. The objective of CSIRT is to execute workflow for responding to the incidents once it is escalated by SOC analysts. The main reason of having a CSIRT is to keep SOC analysts primarily focused on threat monitoring activities instead of getting into response activities which may take long time and may divert their attention away from their primary goal of threat monitoring and detection. A typical high level workflow (corresponding to NIST incident response process) for CSIRT team is shown below that also shows collaboration between SOC analysts and the CSIRT.
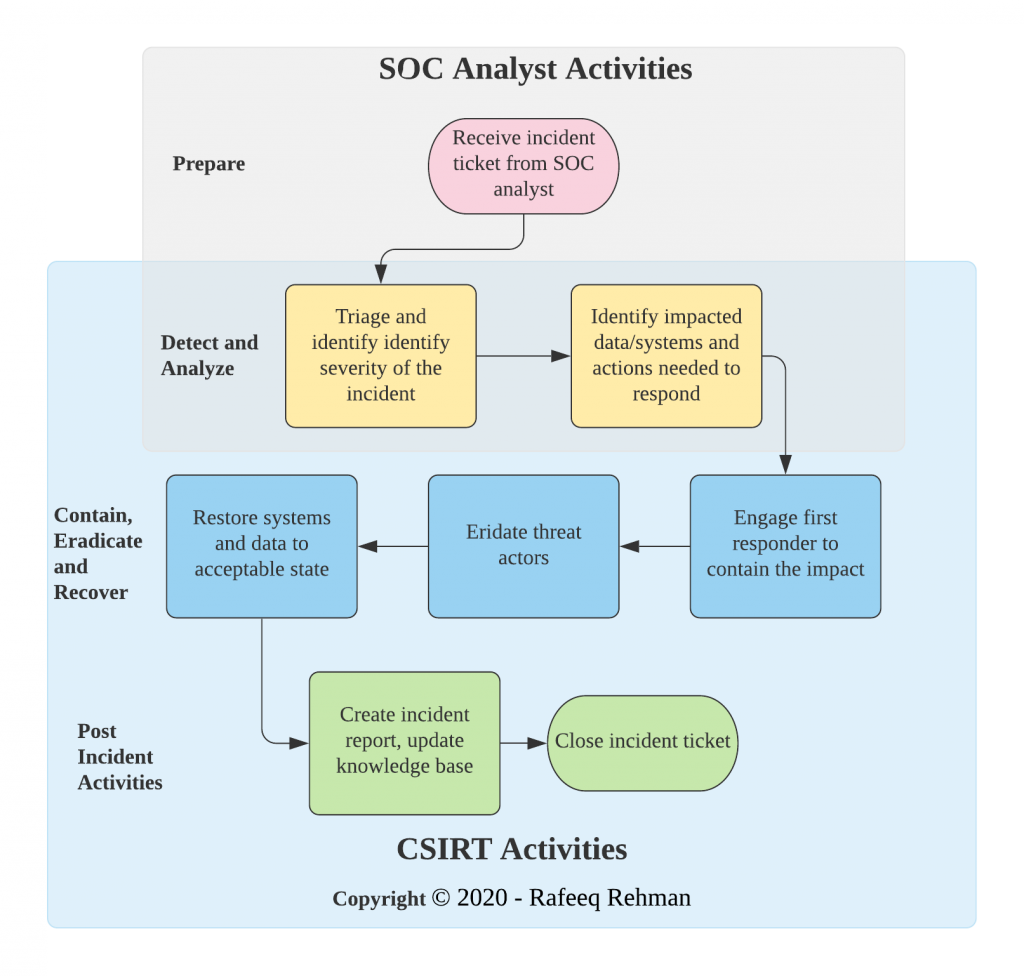
Note than the CSIRT team will be working with the SOC analysts in some phases of the incident response whereas it will take lead in containment, eradication, recovery and post incident activities. However, collaboration among all stakeholders is crucial during incident response and you should not strive for drawing hard lines for where role of one team starts/ends as long as the responders are clear about who is the lead on certain activities.
ENISA and other organizations have published good material about CSIRT establishment, training, and handbooks in case you need further help.