NOTE: A new version of CISO MindMap (2022) is available at this URL.
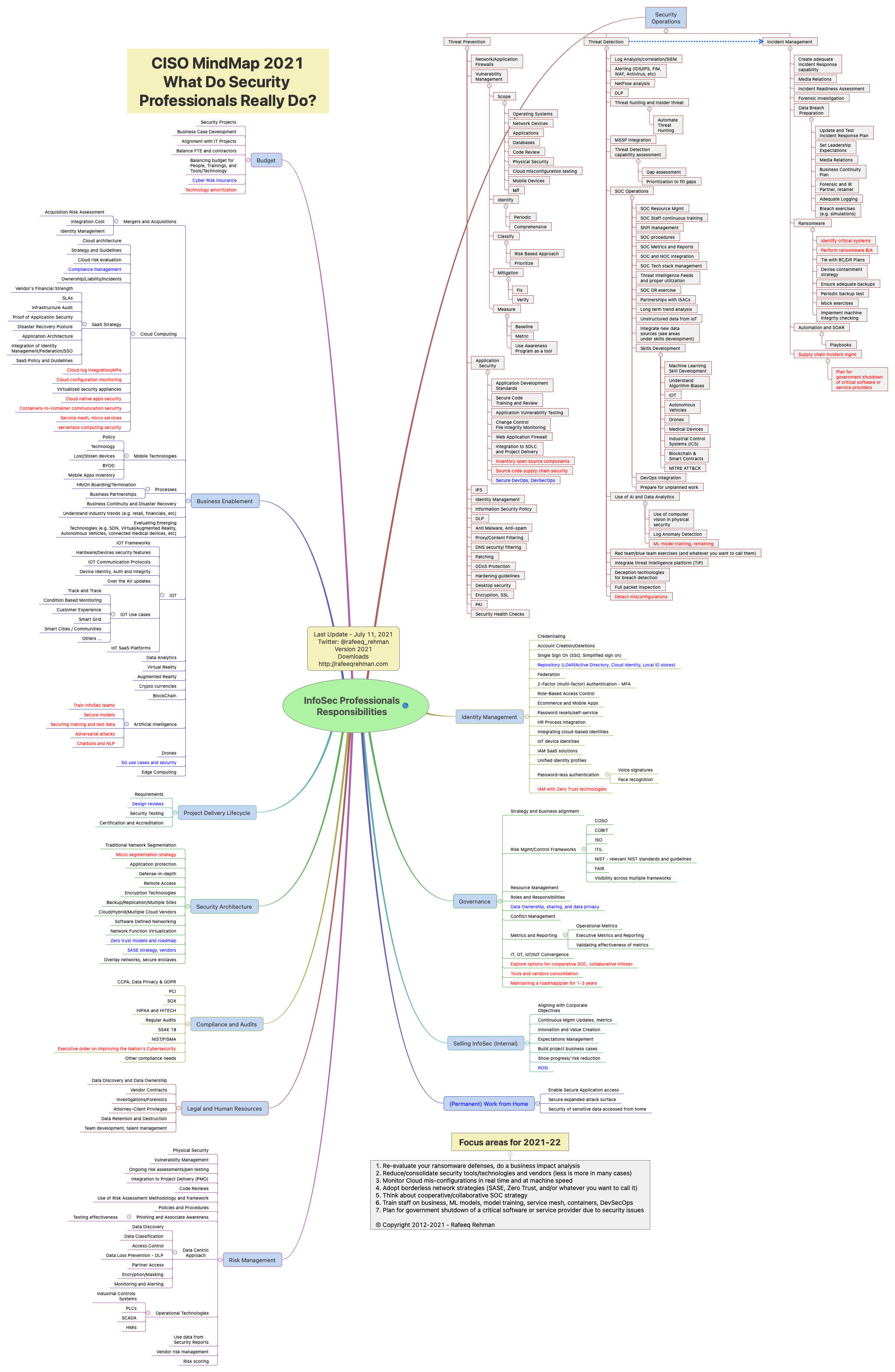
Most people outside the Cybersecurity profession don’t fully realize and appreciate the complexity of security professionals’ job. I have been publishing and updating this MindMap for almost a decade, not only as an effective educational tool but also to enable professionals to use this MindMap for designing and refining their security programs. Here is the latest and updated CISO MindMap for 2021 with a number of updates and new recommendations for 2021-22.
Download CISO MindMap 2021 PDF Version for Printing
What has changed?
The responsibilities of security professionals are only increasing and CISOs are finding themselves in the middle of more things than they wish to be. Why? Technology is changing fast, bringing new ways of doing business, continuous adoption of Cloud, and ever-expanding uses of machine learning (and AI in a broader sense). Infosec professionals are “expected” to not only understand all of this but also provide policies/guidance on security of these technologies. For this reason, every year you find a few new things on the CISO MindMap. This year, I have also reorganized/moved a few items to more appropriate sections. So:
- Items in red color are new that did not exist last year.
- Items in blue color are not new, they are just rearranged in a different section of the MindMap.
I hope this color coding will help you understand what has changed.
Recommendations for 2021-2022
I know you already get plenty of recommendations from your vendors, industry analysts and pundits, and other “experts”. You also know that many of these recommendations may have some vested interests and/or biases. I make my own recommendations as a practitioner every year and try to be objective, avoid the hype, and solely focus on what data and research shows. However, it is still my interpretation of data and facts and I may have my own unintended biases even with all objectivity and an evidence-based approach (by now some of you may have figured out that I am not a machine, although the Age of Spiritual Machines has long been predicted and is on the horizon). For me, the most difficult part while making these recommendations is to pick as few as I can. The following list is longer than what I would like it to be but hopefully it would give you few things to think about.
- Re-evaluate your ransomware defenses, do a business impact analysis, especially in areas where ransomware may impact the physical world and human safety.
- Reduce/consolidate security tools/technologies and vendors (less is more in many cases).
- Monitor Cloud mis-configurations in real time and at machine speed.
- Adopt borderless network strategies (SASE, Zero Trust, and/or whatever you want to call it).
- Think about cooperative/collaborative SOC strategy.
- Train staff on business, ML models, model training, service mesh, containers, DevSecOps.
- Plan for government shutdown of a critical software or service provider due to security issues and supply chain attacks (hope this never happens but supply chain attacks in the past 12 months warrant need for preparedness).
Item number 5 above is a long-term consideration and is not really a new or earth shattering idea. However, it is something to consider seriously for sustainability and to remove some of the insanity in security operations. If you don’t agree, I am eager to listen to your viewpoint and why.
How to use CISO MindMap?
I continuously get messages about how many different ways people are using the CISO MindMap. Over the years, it has become a great tool for many of you and I appreciate your feedback and kudos. Following are some of the ways this MindMap is quite helpful:
- Have you been asked what you really do as a security professional? Well, this is one way for answering the question and explaining it to people. I have heard from many professionals that this MindMap is extremely helpful in explaining the complexity of a CISO job to a business audience.
- A framework for guiding discussion.
- SANS Institute uses it as part of the Security Leadership Poster.
- Designing and refining security programs.
- Some security vendors use the MindMap for awareness.
- CISO group discussions and/or community meetings.
- It could be a great time waster if you have nothing else to do on a Friday evening, or, to say “why would anybody do that”?
Obviously there is a lot on this MindMap. The stress on people who have these responsibilities is real. If nothing else, this MindMap should help leaders recognize that stress and do something about it. I covered this topic (stress) in my latest book Cybersecurity Arm Wrestling: Winning the perpetual fight against crime by building a modern Security Operations Center (SOC) as well.
So let me know what you think about these updates!
Copyright © Note
This is a copyrighted material but is absolutely free to all (like water and air) with no strings attached (as long as it is not altered and not used to make money). My request is that when using this MindMap, please cite the source properly.
Latest Posts
- Run LLM Models on a Macbook
- Navigating the Landscape of Risk Management Frameworks
- CISO MindMap 2024: What do InfoSec Professionals Really Do?
- Building Generative AI (GenAI) Applications
- Security Hygiene