IDC (and other analysts) predict information security, threat intelligence, data analytics, hunting, among others, are expected to grow and become more important part of a CISO’s strategy in 2015 and beyond.
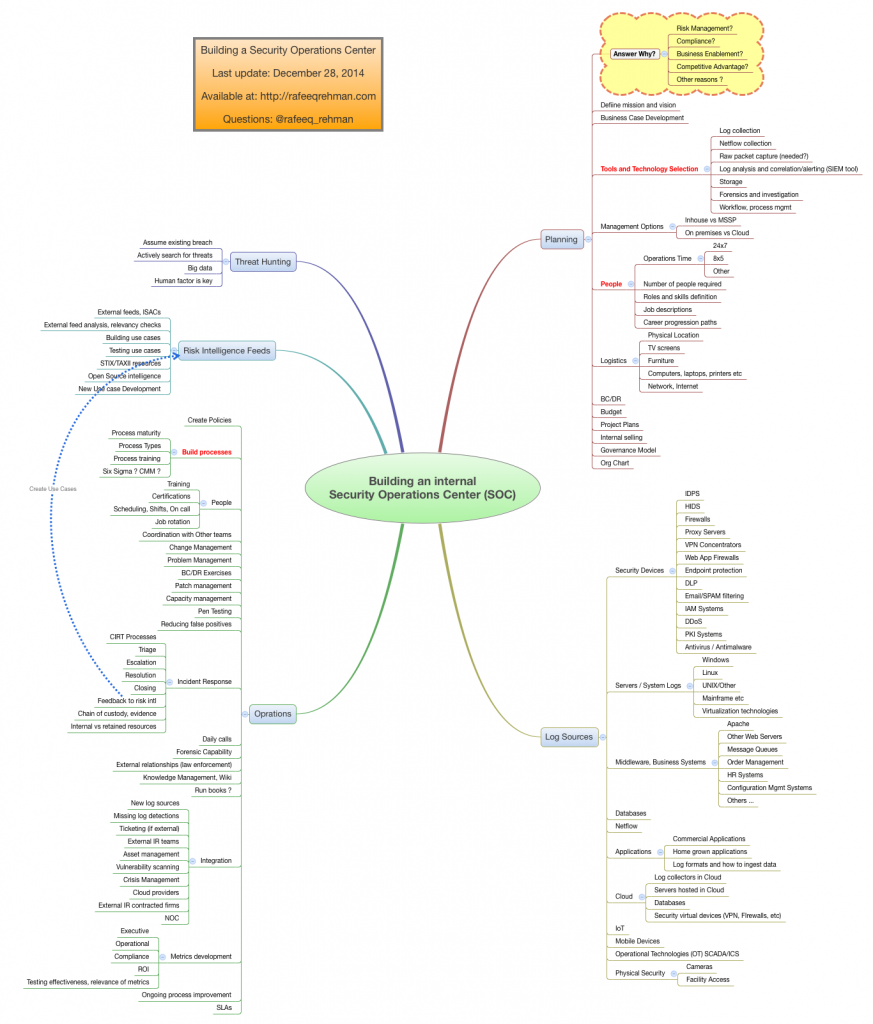
If one has money and backing of a large organization, it is very tempting to build an internal security operations center (SOC) that embodies items listed above. The following mind map is just to make sure that people understand what they are getting into, and think pros and cons of building an internal SOC.
Like everything else in technology, a typical SOC will require three things:
- Technology – Most firms can buy it given sufficient amount of money.
- People – Arguably many firms can hire required people given sufficient amount of money. Keeping them, however, is another matter.
- Processes – SOC requires mature processes. Most of the companies struggle with this. An experienced firm can be very helpful in this area.
Even before getting into the discussion of people, process and technology, if one can’t answer the “Why” part of building a SOC with sufficient convincing detail, please don’t start. That is the reason I highlighted this part in the mind map.
So enjoy the following mind map and if you have any comments, tweet at @rafeeq_rehman. This is PDF Download link.
Your feedback is welcomed on my Twitter handle at @rafeeq_rehman
References