Over years of my professional work and research, I found six ingredients absolutely necessary for success of any SOC, big or small. When you combine these ingredients with continuous improvement activities, you will get excellent business results. On the other hand, you miss one of these and everything falls apart.
For more than a decade since I got involved in helping businesses build security programs and operations centers, it has been quite a learning process. To make this body of knowledge available to the information security community, about two and a half years ago I started writing a book about building a Security Operations Center (SOC). As part of my research for this book. As part of my research, I have interviewed a large number of SOC practitioners, talked to CISOs, read thousands of research papers and reports, explored commercial and open source products, and created tools for budgeting purposes.
So what are those six essential ingredients? While three of them are typical people, process, and technology while others go beyond that as shown in the diagram below.
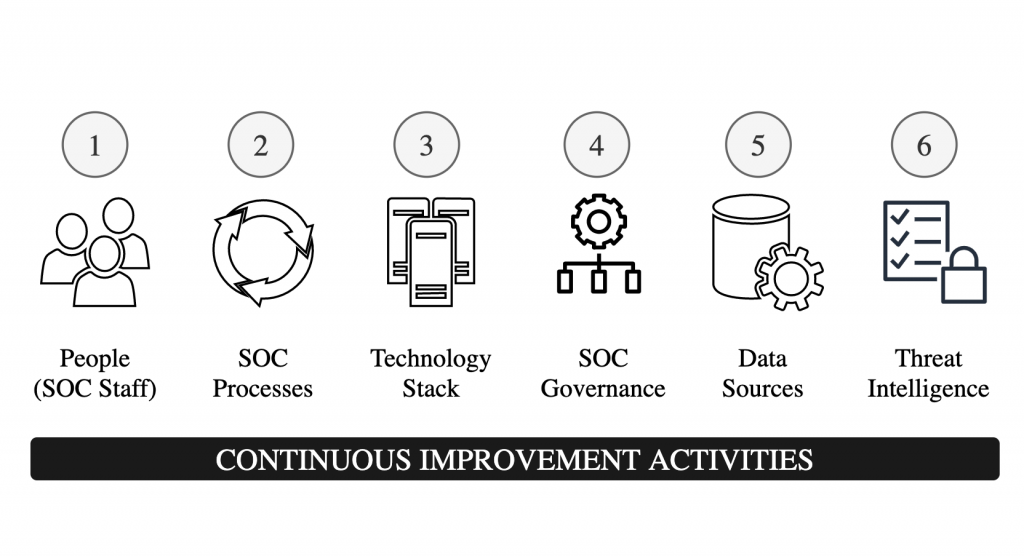
- People (SOC Staff) with different levels of expertise in diverse areas including networking, operating systems, applications, operations management, scripting, Python, vulnerability management, incident handling, forensics and others.
- Defined processes for tasks under the scope of SOC. While there are many SOC processes, effective incident detection and incident management is a key process for success of every SOC. A SOC may also rely on other IT systems/processes like asset management, change management, patch management etc.
- Technology Stack for collecting log and other types of telemetry data, storing data, and processing/analyzing data. Main technologies used in SOC include Security Information and Event Management (SIEM) tool, log collection, network sensing, ticket/incident management, forensic tools, and vulnerability management tools.
- SOC Governance structure that enables SOC management and continuous improvement while ensuring the business objectives of SOC are achieved.
- Carefully selected Data Sources provide high value in threat detection. People need to be careful and selective in determining the type and amount of data that is fed into the technology stack. More is not always better!
- Threat Intelligence is a must for the success of any modern SOC. It helps in proactive threat hunting and helps in automation, responding to threats at machine speed.
While these ingredients are necessary to build a successful SOC, continuous improvement activities are absolutely necessary to keep SOC effective and continuously deliver value. Continuous improvements require that SOC managers look for opportunities of improvement in all of these areas including training of SOC staff.
Also note that while building a SOC, you don’t necessarily need to have all of the SOC components in-house. You can make business decisions about what to keep in-house and where to get help from your security partners/vendors.