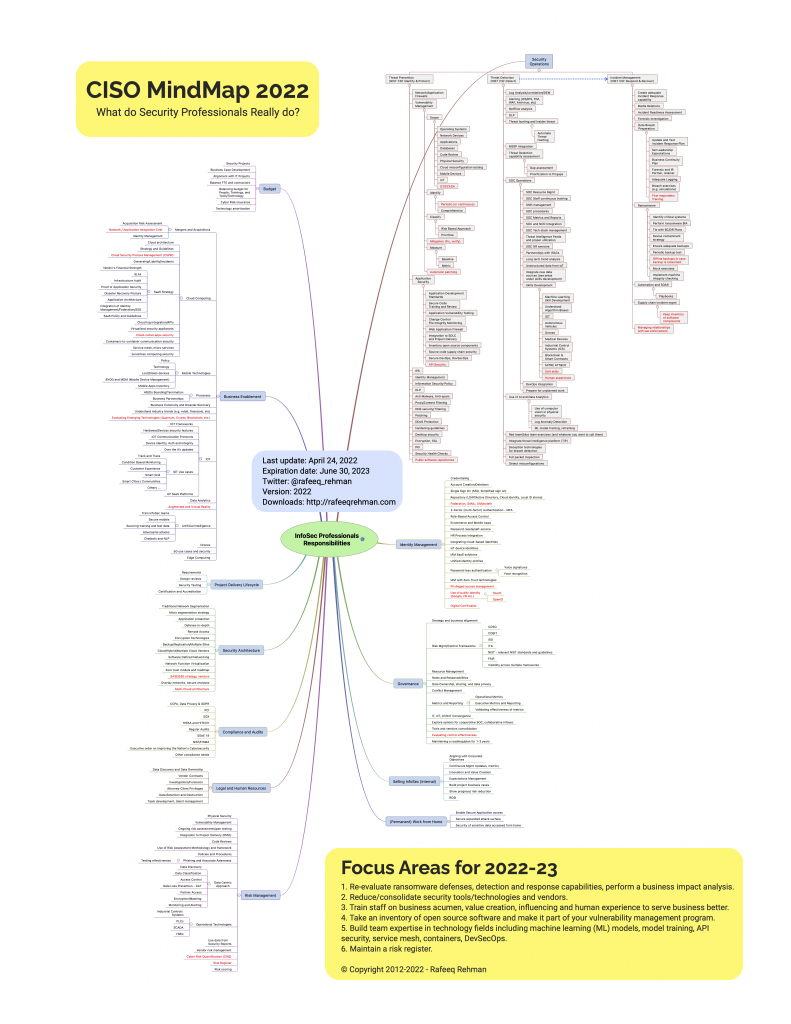
NOTE: A new version of CISO MindMap has been published and is available at this link.
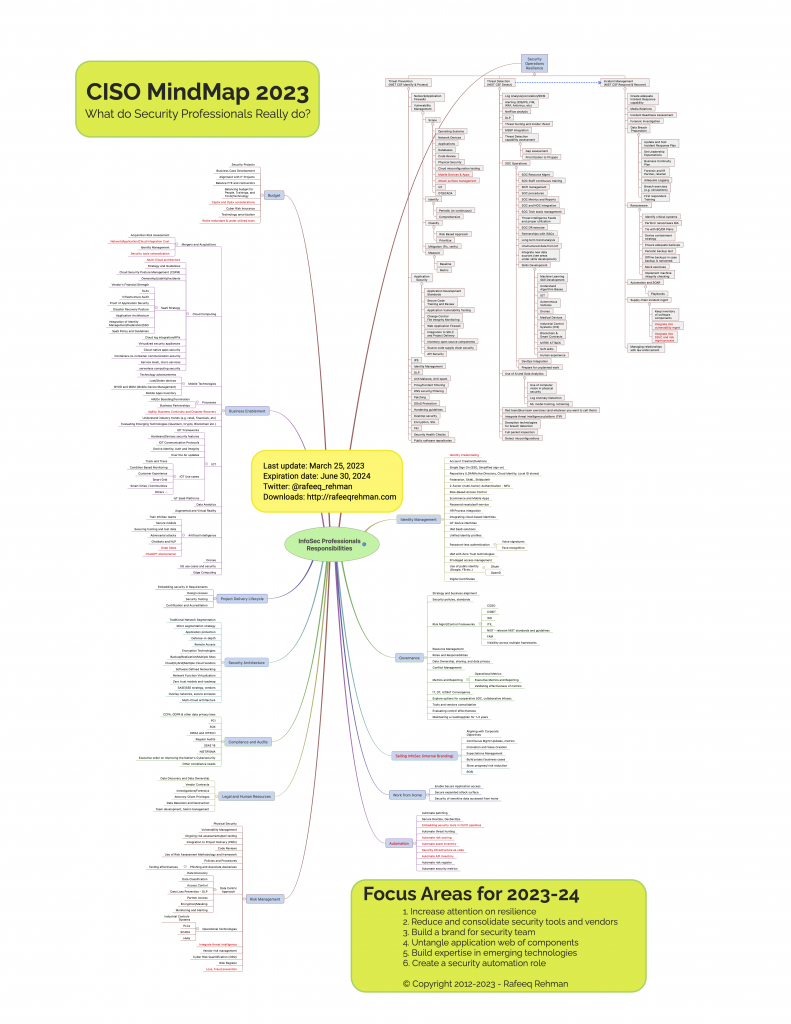
Most people outside the Cybersecurity profession don’t fully realize and appreciate the complexity of a security professional’s job. Since 2012, CISO MindMap has been an effective educational tool to communicate CISO responsibilities and has enabled security professionals to design and refine their security programs. Here is the latest and updated CISO MindMap for 2023 with a number of updates and new recommendations for 2023-24.
Download PDF Version for better printing quality
What has changed?
With time, the responsibilities of security professionals are only increasing. Why? Technology is changing fast, bringing new ways of doing business, continuous adoption of Cloud, and many emerging technologies like ChatGPT phenomenon with many vendors working on similar solutions. Not only the Infosec professionals are “expected” to deeply understand these technologies, but also provide policies/guidance on how to secure them. For this reason, every year you find new things on the CISO MindMap. Like every year, few things are added, changed or removed from the CISO MindMap depending upon their relevance. Modified and new items are marked in red color for your convenience.
Other changes include but not limited to:
- Automation – A section on “Automation” is added after re-organizing some existing content and adding new. Given efforts of optimization of budget by many CISOs and lack of qualified staff, automation is key to remove routine tasks and find efficiencies in security operations. I believe every security team must create a specific role for automation
- Redundancy and Overlaps – Remove some redundancies and overlaps
- Expiration Date – A common issue is that many professionals still have older CISO MindMap copies. I added an “expiration date” to let people know when they should stop using a particular version. The expiration date for the 2023 CISO MindMap is the end of June 2024. The next version will be published before the current version expires.
Recommendations for 2023-2024
Every year I make my recommendations as a practitioner and based upon conversations with infosec leaders. I try to be objective, avoid the hype, need for adoption in the next 12-18 months, and solely focus on what data and research shows. While there may be some unintended biases, the objective is to provide actions that can be taken in a short to mid range time period. These are not “predictions” of the future but rather “what is needed now” to strengthen security programs.
For me, the most difficult part while making these recommendations is to pick as few as I can. The following list is longer than what I would like it to be but hopefully it would give you a few things to think about. The followers of MindMap would quickly realize that some of these are the same as previous years and some new ones.
- Increase Attention on Resilience – Evaluate ransomware defenses, detection and response capabilities, perform a business impact analysis and identify critical processes, applications and data. Test ability to restore systems and data within an acceptable time frame. Understand that merely having a backup is not enough. Ability to rebuild impacted systems and restore backups in a timely manner is crucial to bring business back to normal operating conditions after security incidents.
- Reduce and Consolidate Security Tools – More security tools don’t necessarily reduce risk but do add the need for maintaining expertise on security teams. While deciding which tools to keep or retire, think about functionality overlap, future direction, innovation on the part of vendors
- Build a Brand for Security Team – While the message is important, the credibility of the messenger is also crucial. To serve business better, train security team staff on business acumen, value creation, influencing people without authority, and human experience. I included this recommendation last year as well and we need to keep focus on the fact that information security teams don’t live in a vacuum and have to enable business and interact with others.
- Untangle Application Web of Components – Modern applications have become a web of interconnected components, APIs, multiple cloud and data centers, open source libraries, third party services like DNS, email, content delivery vendors, and so on. Even when you purchase a commercial off the shelf application/software, it may rely on third party APIs and services. Understand how business applications work, take an inventory of all components that they rely on, and make it part of your vulnerability management program.
- Build Expertise in Emerging Technologies – By now everyone has heard about ChatGPT and competing technologies from other vendors. Build team expertise in technology fields including machine learning (ML) models, model training, API security, service mesh, containers, DevSecOps.
- Create a Security Automation Role – Managing security program cost and working at “machine speed” requires automation. This is a new section added to CISO MindMap this year. Automate maintaining a risk register, asset (hardware, software, APIs, etc.) inventory, scanning and testing. Many tools used in CI/CD pipelines as part of DevOps are useful for automation. However, simple scripting goes a long way in reducing overhead of routine tasks. I would highly recommend automating security metrics such that you can see the current state of your security program anytime you need to, almost in real time. It is not an easy task but it is doable. I have observed some organizations do it on scale.
I am eager to listen to your viewpoint on these recommendations, why or why not!
How to use CISO MindMap?
It is unbelievable how many posts and messages I see about many different ways people are using the CISO MindMap. Over the years, it has become a great tool for many of you and I appreciate your feedback, suggestions for improvements. Following are some of the ways this MindMap is quite helpful:
- Have you been asked what you really do as a security professional? The CISO MindMap is one way for answering the question and explaining it to people. I have heard from many professionals that this MindMap is extremely helpful in explaining the complexity of a CISO job, especially to a business audience.
- A means for guiding conversation with other technology professionals.
- SANS Institute uses it as part of the Security Leadership Poster.
- Designing and refining security programs.
- Some security vendors use the MindMap for awareness.
- CISO group discussions and/or community meetings.
- For aspiring security professionals, understand the landscape and decide their career path.
- An educational and awareness tool.
Obviously there is a lot on this MindMap. The stress on people who have these responsibilities is real. If nothing else, this MindMap should help leaders recognize that stress and do something about it. I covered this topic (stress) in my latest book Cybersecurity Arm Wrestling: Winning the perpetual fight against crime by building a modern Security Operations Center (SOC) as well.
What do they say?
Many security leaders and professionals have made comments on LinkedIn about CISO MindMap and how they use it. Following is a sample of some of these comments with links to original posts on LinkedIn.
Jesper Bork Olsen said:
“Interested in understanding the role of a CISO? Today, reflecting on the past weeks of intensity, curiosity and just overall well invested energy, I enjoy looking through the newly updated CISO mindmap that Rafeeq Rehman continues to maintain both from a relevance, recommendations and a reminding perspective.
If you’re in the #cybersecurity field you will have seen the #CISO mindmap for sure, and if you are a senior leader, that haven’t had the pleasure yet or are curious as to what a CISO actually considers in the everyday life, I strongly recommend spending time on this – I guarantee there are topics on there that can inspire a vivid conversation with the board in almost any organization! If nothing else, share the 6 recommendations with your cybersecurity team and see if it’s a match for you too 😉
For me personally, the Mindmap has served as a great source of inspiration from the very first version several years ago – thank you Rafeeq Rehman for your continued contributions to the community!!”
Rodolphe Simonetti said:
“My friend Rafeeq Rehman recently released the 2022 version of the CISO Mindmap – always a great reference.”
Dan Maslin Wrote:
“Another year, another update to the CISO MindMap by Rafeeq Rehman. Looks like in 2022 we’ve added another dozen or so areas of responsibility for the CISO (unsurprising and yes it is unrelenting), these are shown in red.
Published now for over a decade, I find these CISO MindMaps incredibly useful to explain (maybe to ourselves at the very least) the breadth and complexities of the roles that CISOs and cyber security teams undertake.”
Martin tePoele says:
“I ran across the CISO MindMap recently and was quite impressed.”
David Howell says:
“Landed on a great resource for anyone interested in better understanding the incredibly complex scope of responsibilities under a CISO. The CISO Mind Map (courtesy of Rafeeq Rehman) puts it all into perspective. It’s one thing to say “CISOs have a lot on their plates” – but another thing to see it in black and white. The CISO Mind Map is also useful in terms of thinking about how the many discrete activities and programs may be organized.”
Acknowledgments
In addition to numerous infosec leaders who provide their input, we have a LinkedIn Group to gather suggestions and comments from the community. While many provided feedback, the following is an alphabetically organized list of people and organizations who provided “specific suggestions” for improvements. If I missed anyone, please send me a message to make corrections.
- Alan Ng
- Aldo Febro, PhD
- Andi Baritchi
- Ashok Kakani
- Charles Gillman
- David Cowper
- Matthew Thompson
- Ron Precilla
- Rodolphe Simonetti
Your input is highly appreciated!
Copyright © Note
This MindMap is copyrighted material. However it is absolutely free to all (like water and air) with no strings attached (as long as it is not altered and not used to make money). When using this MindMap, please cite the source properly so that recipients can receive future updates.
Subscribe to my blog
To keep updated about new posts, you can subscribe to my blog